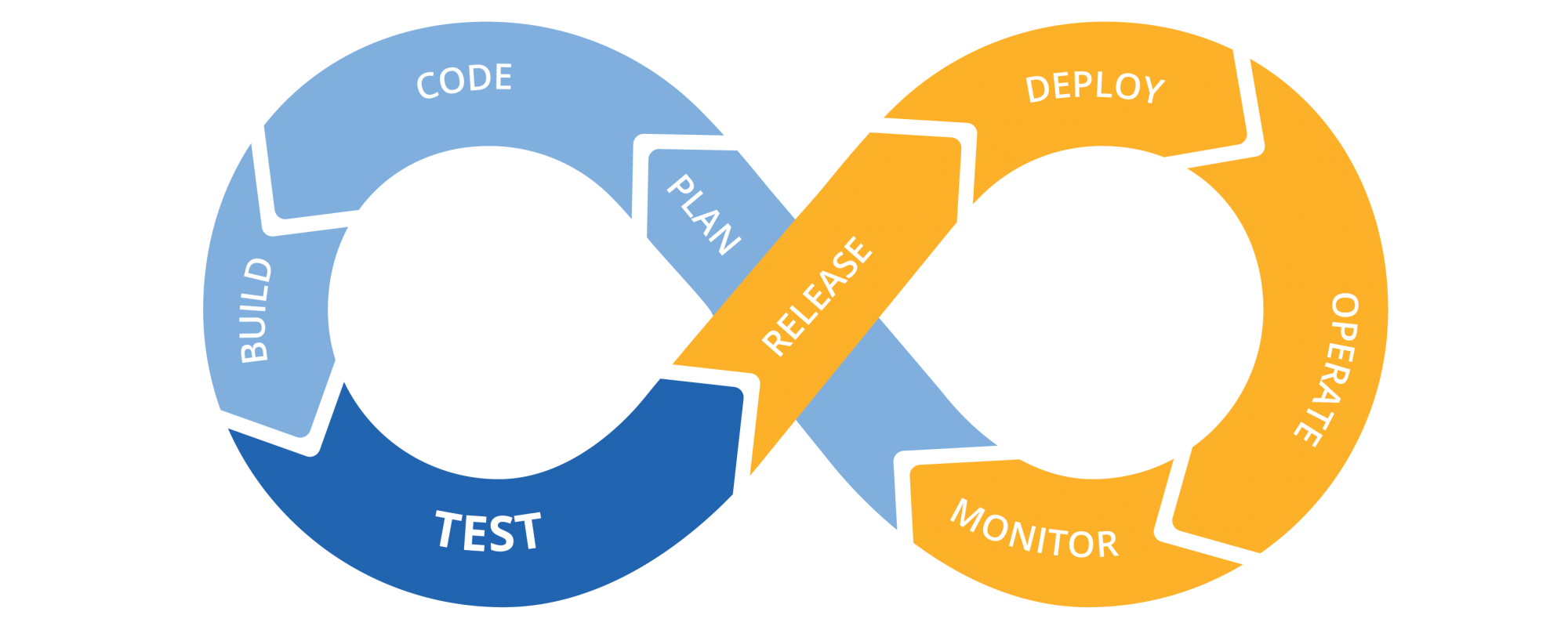
Microservice Options to Consider
Service discovery tools for microservices 6 Microservices Options You Need To Consider Microservices is a software development technique that focuses on breaking applications into discrete and separate services within the wider...
Read More