Wouldn’t you know it. Just as demand for mobile fintech services explodes, the familiar and unwelcome sight of security weaknesses rears its ugly head. The constant demand for robust, secure services...
Read MoreNetwork Security
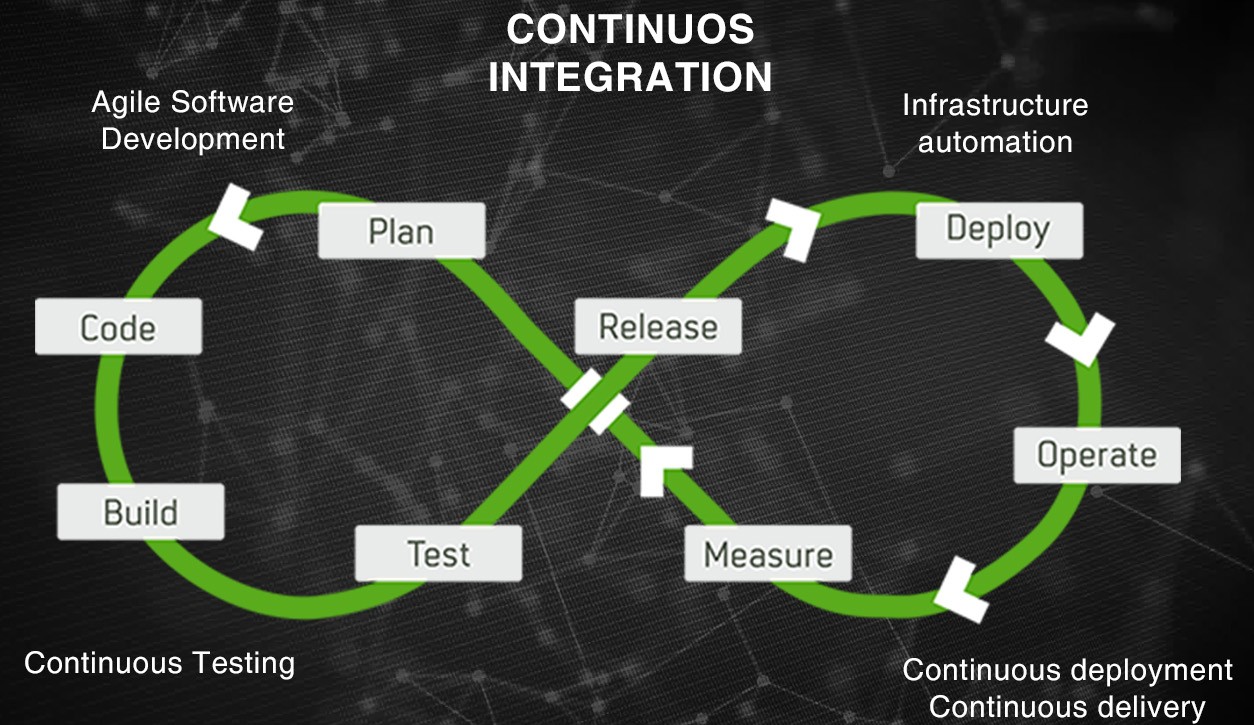
Continuous integration (CI) and continuous deployment (CD) are powerful strategies that your software team needs to adopt, if it hasn’t currently already. How would you like a simple, low-cost path...
Read MoreWe’ve known this was coming for a while. Security experts have spent the last several years warning us about it. Yet somehow, when the Internet was brought screeching to a...
Read MoreIf you’re reading this, you have already identified the need for data center “space.” The question that should continue to be asked is “Can I justify this?” at every step...
Read MoreMobile malware is on the rise. According to a recent Kaspersky survey, malicious software targeted at mobile devices increased by nearly 1.7 times between Q1 and Q2 2016. It’s an...
Read MoreIt’d be nice if every single security threat that faced your organization was glaringly obvious - a massive botnet here, poorly-disguised malware there. Unfortunately, in the real world, things are...
Read MoreLast year, I wrote a piece about how the Internet of Things could pave the way for some of the biggest botnets in history. I take no pleasure in the...
Read MoreNot everything is peachy-keen in the cloud. Did you know that as many as 10% of cloud repositories may be infected by malware? That includes those hosted by Amazon and Google,...
Read MoreSince the 1980s, ransomware - an attack method in which malicious software locks down a user’s PC and files until they pay a set amount to the attacker - has...
Read MoreThere’s no such thing as a truly infallible system. Every platform, no matter how extensive or powerful, has points of failure. The Amazon Web Services outages we’ve seen over the...
Read More- 1
- 2